OAuth 2.0 is a widely used authorization framework that allows applications to access resources on behalf of a user without exposing their credentials. The diagram you provided visually represents the four primary OAuth 2.0 authorization flows: Authorization Code Flow, Implicit Flow, Resource Owner Password Credentials Flow, and Client Credentials Flow. Let’s explore each flow in detail to understand how they work and their respective use cases.
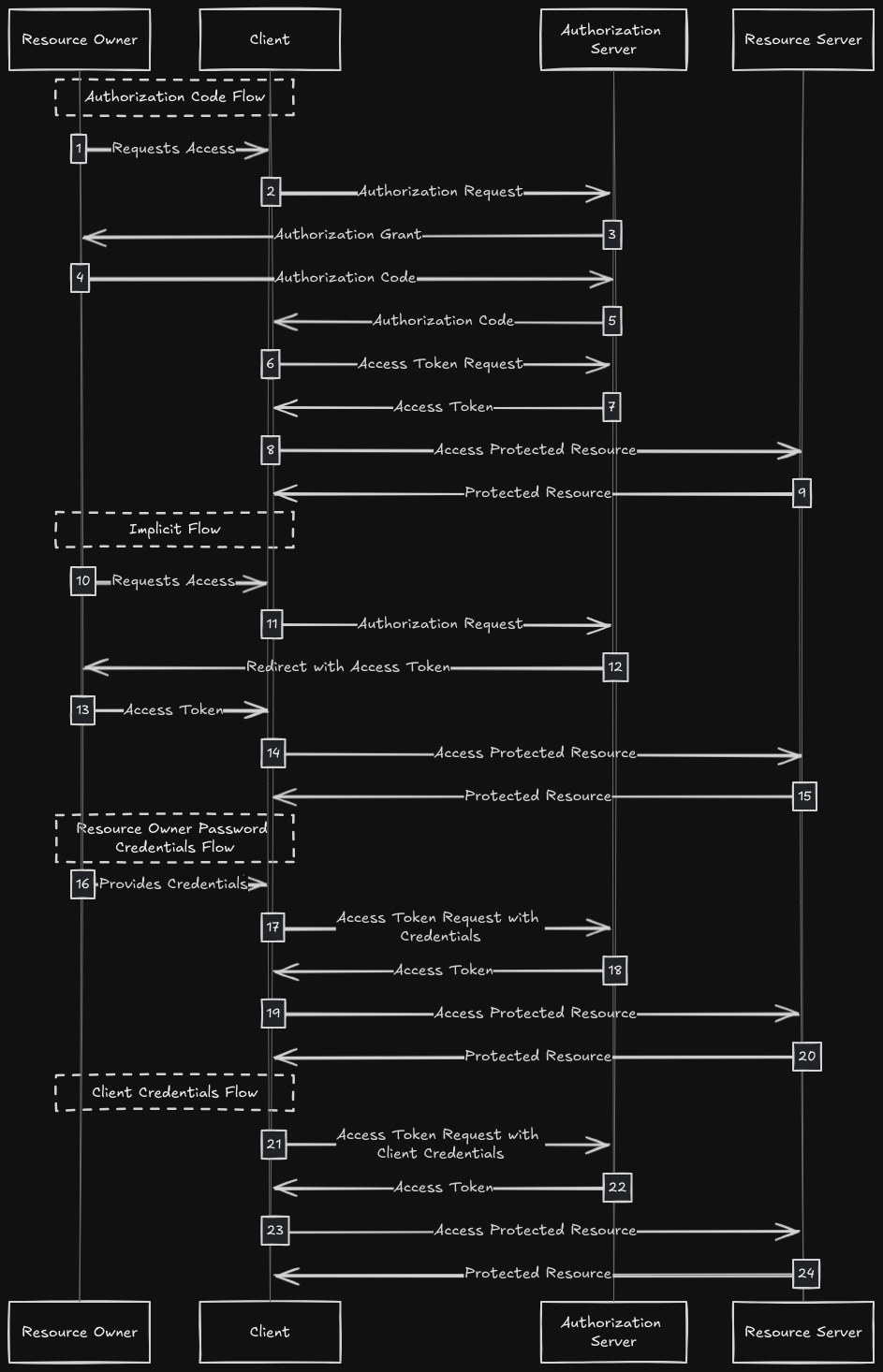
1. Authorization Code Flow
Use Case: This flow is ideal for web and mobile applications where the client can securely store a client secret.
Steps:
- Request Access: The client application requests access to a resource.
- Authorization Request: The client redirects the resource owner (user) to the authorization server with an authorization request.
- Authorization Grant: If the user approves, the authorization server grants an authorization code.
- Authorization Code: The client receives the authorization code and uses it to request an access token.
- Access Token Request: The client sends the authorization code to the authorization server, along with the client secret, to request an access token.
- Access Token: The authorization server verifies the code and client credentials, then issues an access token.
- Access Protected Resource: The client uses the access token to request the protected resource from the resource server.
- Protected Resource: The resource server verifies the access token and provides the requested resource.
2. Implicit Flow
Use Case: Suitable for single-page applications (SPAs) where the client cannot securely store a client secret.
Steps:
- Request Access: The client application requests access to a resource.
- Authorization Request: The client redirects the user to the authorization server with an authorization request.
- Redirect with Access Token: The authorization server directly redirects the user back to the client with an access token in the URL.
- Access Token: The client extracts the access token from the URL.
- Access Protected Resource: The client uses the access token to request the protected resource from the resource server.
- Protected Resource: The resource server verifies the access token and provides the requested resource.
3. Resource Owner Password Credentials Flow
Use Case: This flow is used in highly trusted environments, like first-party applications, where the resource owner trusts the client with their credentials.
Steps:
- Provides Credentials: The resource owner directly provides their credentials (username and password) to the client.
- Access Token Request with Credentials: The client sends the resource owner’s credentials to the authorization server, requesting an access token.
- Access Token: The authorization server verifies the credentials and issues an access token.
- Access Protected Resource: The client uses the access token to request the protected resource from the resource server.
- Protected Resource: The resource server verifies the access token and provides the requested resource.
4. Client Credentials Flow
Use Case: Suitable for machine-to-machine (M2M) communication where the client application needs access to resources not tied to a specific user.
Steps:
- Access Token Request with Client Credentials: The client sends its credentials (client ID and secret) to the authorization server, requesting an access token.
- Access Token: The authorization server verifies the client credentials and issues an access token.
- Access Protected Resource: The client uses the access token to request the protected resource from the resource server.
- Protected Resource: The resource server verifies the access token and provides the requested resource.
Conclusion
Understanding these OAuth 2.0 flows is crucial for implementing secure authentication and authorization in your applications. Each flow has its specific use case, and choosing the right one depends on your application’s architecture and security requirements.
- Authorization Code Flow is best for applications that can securely store secrets.
- Implicit Flow is optimized for clients that cannot securely store secrets, such as SPAs.
- Resource Owner Password Credentials Flow should only be used in trusted environments.
- Client Credentials Flow is the go-to for M2M communications.